A new type of phishing attack is targeting Berkeley Lab users through Google Calendar. Attackers are sending fake calendar invites, taking advantage of Google’s default setting that automatically adds invitations to your calendar.
What is the attack
This phishing technique uses Google Calendar invitations to deliver scams directly to your calendar. Because Google automatically adds calendar invites by default, attackers can make these events appear genuine, showing them alongside your real meetings.
Common examples of fake calendar events include:
- “Your password is expiring – verify immediately”
- “Security alert: unauthorized login detected”
- “Invoice processed – payment confirmation”
- “Prize notification – claim your reward now”
Here is a few examples:
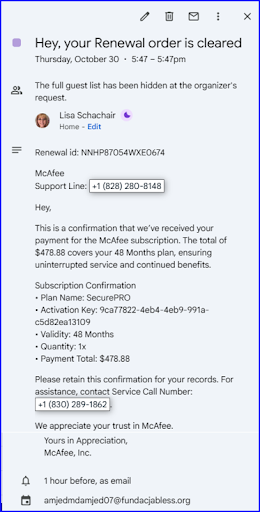
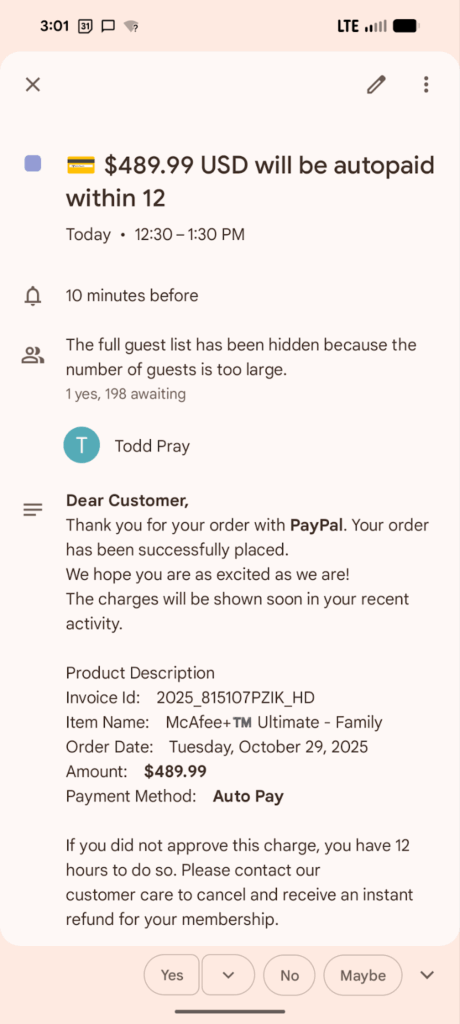
How does the attack work
Attackers exploit Google’s default setting that automatically adds new calendar invitations to your schedule. When a user receives an invite, even from an unknown sender the event appears in their calendar, often with an urgent message in the description.
These descriptions can contain:
- Fake phone numbers claiming to connect to support or billing departments
- Malicious links to phishing websites or fake login pages
- Urgent or alarming messages designed to prompt quick action
Once a user clicks a link or calls the number, the attacker can try to steal login credentials, financial information, or remote access to the computer.
What is the attacker trying to trick you into and why
In short, attackers disguise their phishing lure as a harmless calendar event to get your attention. The attacker’s goal is to get you to contact them, where the real attack occurs. They will attempt to extract credit card details or login information if you call the phone number or click any links.
By exploiting a familiar platform you use daily and naturally consider safe, such as Google Calendar to take advantage of the false sense of security you may feel when using it.
How to Spot the Attack
Watch for these red flags in suspicious calendar invitations:
- Titles can reference anything but focus on invoices and calls to action. These types of invite titles can look more like email titles. Following are some examples:
- “Processing Complete: Bill INV936377”
- “Your password is expiring – verify immediately”
- “Prize notification – claim your reward now”
- The organizer is not someone you know or does not have an lbl.gov email address.
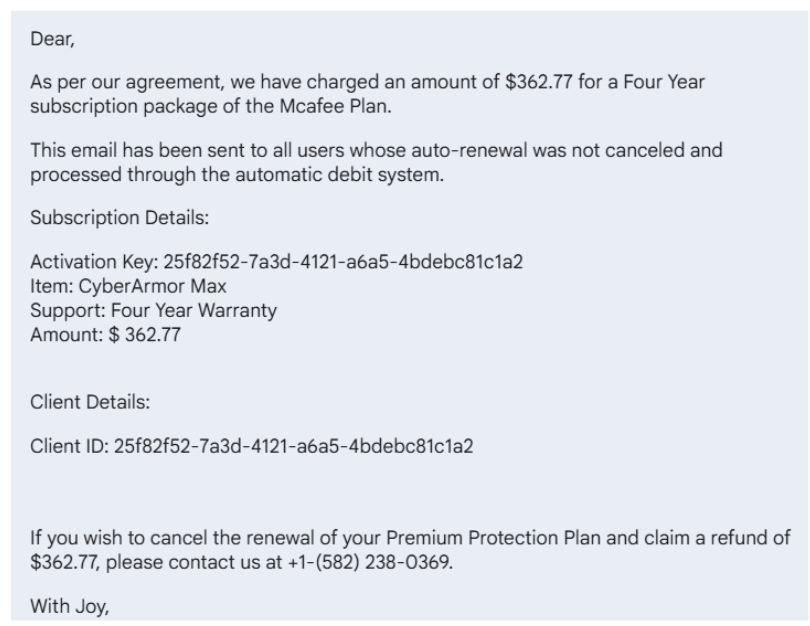
- The event description can often include a phone number to “cancel” or “secure a refund” or a malicious link they want you to use. Here is an example:
What to Do if You Receive a Suspicious Google Calendar Invite
- Report and delete the event. Use Google’s “Report Spam” feature
- Do not engage. Never click links, call phone numbers, or reply to a suspicious event because they could get access to your personal or business-related information.
- Do not select “Accept” or “Decline”. This confirms your email address is active and can lead to more spam.
How to Potentially Prevent Future Calendar Scams
Some people put in higher levels of protection by limiting who can add events to your Google Calendar. To do this, follow these steps:
- Open Google Calendar in your web browser.
- Click the gear icon in the upper-right corner and select Settings
- In the left-hand menu, choose Event settings.
- Under “Add invitations to my calendar,” select either:
- Only if the sender is known, or
- When I respond to the invitation email.
However, there are downsides to creating this level of protection. While limiting who can automatically add events to your calendar helps protect against phishing scams, it may also change how legitimate invitations behave. Following is a list of the potential pitfalls of adding that layer of protection:
- Legitimate invites might not appear automatically: If you choose “Only if the sender is known” or “When I respond to the invitation email,” invitations from people outside Berkeley Lab, our new collaborators won’t show up on your calendar until you take action.
- You might need to manually accept more invites: You’ll have to open the invitation email and click “Yes” to add it, which adds an extra step for meetings, especially from external partners or conference organizers.
For some, the benefits outweigh the drawbacks for most users, especially given the rise of calendar-based phishing attacks, but it’s important to understand that you’re trading a bit of convenience for added protection.
If you frequently collaborate with external partners, you can balance security and usability by choosing “Only if the sender is known” (rather than the stricter “When I respond”) and staying vigilant when reviewing event emails.

