-
IT Launches New Support Portal
Berkeley Lab’s IT Division launched a new support portal this month. This user-friendly service platform is designed to make opening IT tickets easier than ever. The new portal provides greater transparency, faster access to key information, and an improved overall support experience for everyone. You can access the new IT Support portal using your Berkeley… Read more »
-
(Completed) Thursday, March 4, 2021 – IdM Maintenance Outage
Identity Management systems will be undergoing maintenance from 7:00 PM to approximately 9:00 PM on Thursday, March 4.While most redundant applications are expected to continue to operate normally, there is the possibility of brief outages.These systems include all the IT Division’s authentication services, including Single Sign-On, Phonebook, RADIUS (Employee Wireless and VPN), and Multifactor Authentication… Read more »
-
[Completed] Wednesday, February 24, 2021 smtp.lbl.gov change
On February 24, 2021, smtp.lbl.gov was reconfigured as a CNAME alias that uses Google’s SMTP relay service (smtp-relay.gmail.com) instead of being an on-the-hill host (131.243.228.39).Any on-the-hill systems (ie having an LBL Class B or NERSC IP address) will still be allowed to relay unauthenticated via smtp.lbl.gov and do not need to change their outgoing/outbound SMTP settings.This change will only… Read more »
-
macOS Big Sur is unblocked! But wait!
Hold on! Before you rush to upgrade, here are the things to do:MacOS Big Sur compatibility: Find out if your device will work with the new OSSoftware that has been tested for macOS Big Sur on M1 ChipsetCheck software compatibility for macOS Big Sur on Intel ChipsetAre all your peripheral devices compatible?Is all your installed… Read more »
-
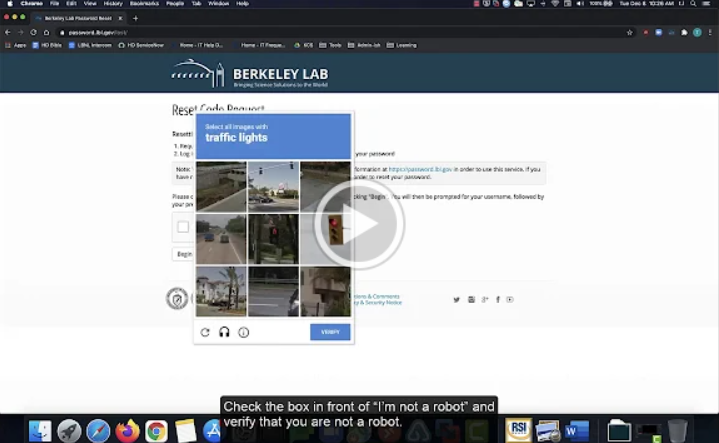
New Video Tutorials!
Announcing our new video tutorials to help you solve common computing questions! You will begin to see videos listed in our FAQ pages. IT has created the following help videos to assist you: How to Reset LDAP Password Resync a Yubikey Installing VPN on Windows Installing VPN on Mac Installing VPN on ChromeOS Add a… Read more »
-
Atlassian and Trello emails Feb 2021
By Jay Krous Summary The Atlassian and Trello emails were a vendor mistake, you can ignore them. If you reported this to security@lbl.gov, that was a reasonable step as this was indeed suspicious; we appreciate your vigilance. Background On Feb 9, 2021 Atlassian and Trello sent a number of confusing emails to every account at the… Read more »
-
Releasing Big Sur Upgrade
Berkeley Lab IT will be releasing the block on Big Sur for macOS. IT initiated the block to address software incompatibilities, more specifically with the Lab’s anti-virus software Sophos. Those issues can now be resolved by upgrading your Sophos client with the latest version from our Sophos server. For further information and other related postings… Read more »
-
What Works and Doesn’t Work on macOS Big Sur and Mac M1 Silicon Chipset
Berkeley Lab IT did some recent software compatibility testing of Big Sur with common applications used at LBL. Tests run on a MacBook Pro 13” with new M1 chipset and macOS Big Sur 11.0.1. Results listed below:Test StepsTest ResultsDownloaded Latest ChromeInstalled ChromeChrome prompts user to select between “Intel” or “M1”Browser installed, no issue Downloaded Latest FirefoxInstalled… Read more »
-
New Help Videos: update macOS & Windows, configure IP address for Windows
IT has created new videos to help you with:How to configure static IP address for WindowsHow to run Windows 10 updateHow to run macOS updateIf you would like to see a specific help video created, let us know!Keep an eye on our IT Spotlight page for future announcements on new video tutorials! Read more »
-
New Help Videos: Add a Printer on macOS, Reset AD Password, Map Network Drive on Windows!
IT has created a new video to help you with:Adding printer for macOSHow to reset AD passwordMap network Drive for Windows 10If you would like to see a specific help video created, let us know!Keep an eye on our IT Spotlight page for future announcements on new video tutorials! Read more »
-
New Help Videos: Configure IP Address, Map Network Drive on macOS!
IT has created new videos to help you with:How to configure static IP address for macOSHow to map network drive for macOSIf you would like to see a specific help video created, let us know!Keep an eye on our IT Spotlight page for future announcements on new video tutorials! Read more »
-
IT has posted a new video for adding printers for Windows!
IT has created a new video to help you with adding a printer for Windows.You can find it on our FAQ page along with our written instructions here:Download Toshiba Printer for WindowsAdd printer with Active Directory for WindowsAdd local printer without Active Directory for WindowsIf you would like to see a specific help video created, let… Read more »
-
AWS Machine Learning Day
Dear LBL Cloud Users, On Friday 1/29 from 8am-3pm, Science IT has made arrangements with the Lab’s AWS Team to host a Machine Learning Immersion Day for LBNL researchers, please see the agenda below: Date: Friday, January 29 Time: 8:00am-3:00pm Location: https://chime.aws/1747421123 8:00am – 9:00am PST: Introductions of AWS Team and ML Overview on AWS 40 min… Read more »

Keep in Touch
Continue visiting our website to view the latest in IT news and updates impacting Berkeley Lab staff and affiliates.
Contact IT Communications at itcomms@lbl.gov for questions and feedback regarding IT news, the IT website, or monthly newsletter.