By Arica Chhay, Jay Krous

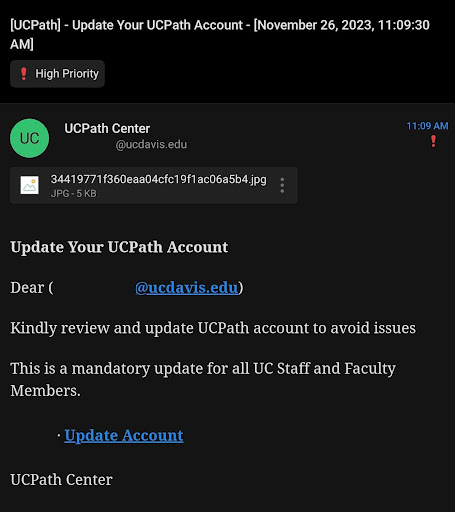
A recent phishing attack impersonated UCPath and targeted employees at multiple campuses. While there was no financial loss, you should stay alert and learn how to spot phishing attempts to keep yourself and the Lab safe. Read more for an overview of the UCPath incident and to view an example of a recent phishing attempt.
Background
Starting on November 26, 2023, employees at multiple UC campuses reported phishing emails appearing to come from UCPath, the systemwide payroll, benefits, and human resources center.
Several red flags make it clear to the observer that the emails are suspicious:
- The attackers used the name, “UCPath Center” for a non-UC email address and included “Update Your UCPath Account” in the subject line. Utilizing names of well-known, legitimate entities builds trust, pushing you to click fraudulent emails without verifying authenticity of the sender and message.
- A sense of false urgency is created by claiming the request is mandatory and that issues may occur if you do not take action.
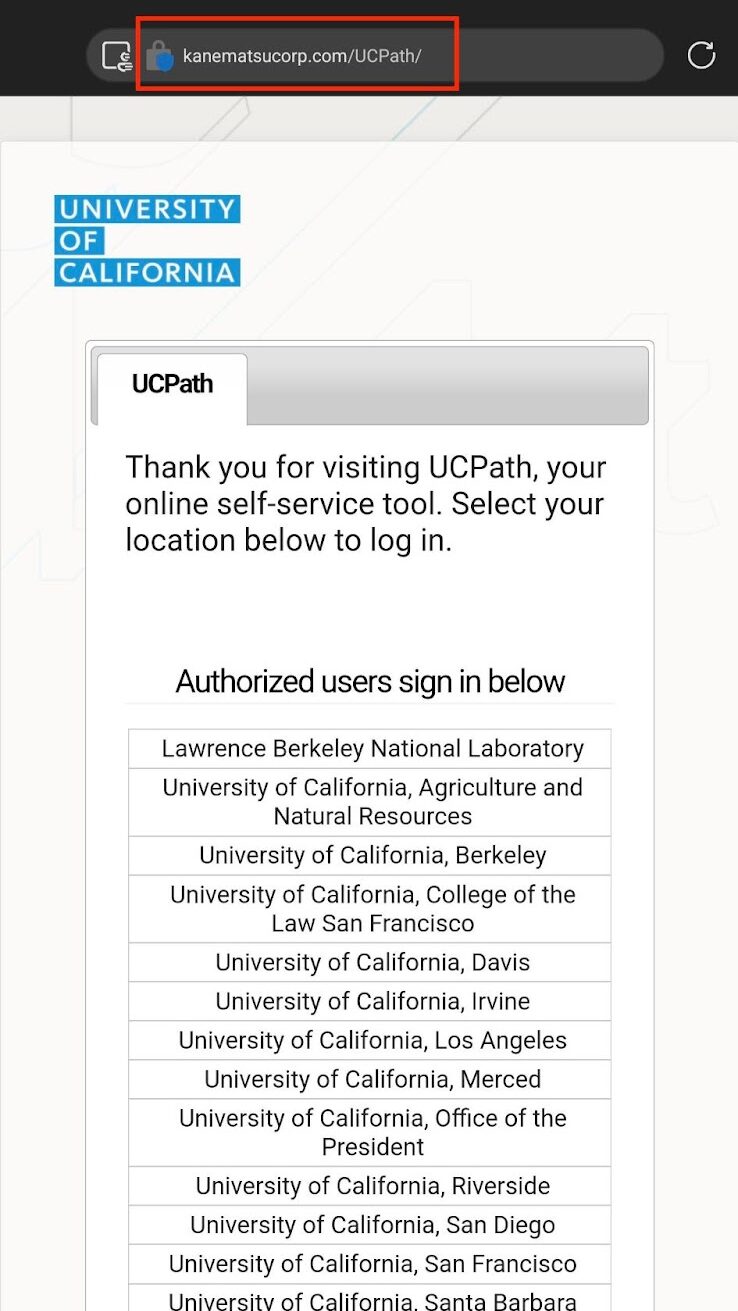
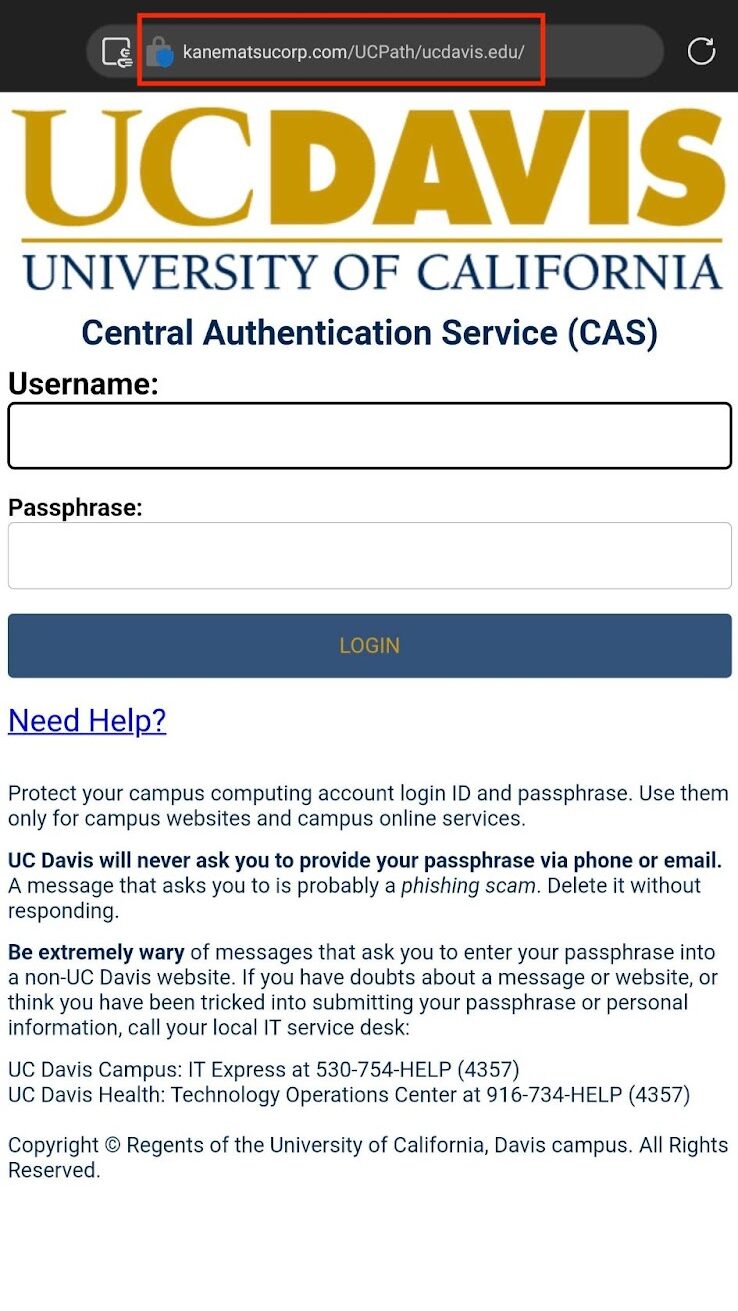
- The link to update your account points to a fake login page with a non-UC web address. Take a second to check links carefully before clicking. Target links can be viewed by hovering over the link text on your computer browser.
- Initial phishing emails were sent on Sunday of Thanksgiving weekend. It’s common for scams to ramp up during the holiday season, when people are busy and distracted.
- The format of the phishing email and lack of details doesn’t match the language and style of official UC service communications.
A malicious link in the email sends users to a fake UCPath login page.
The fake UCPath login page linked in the phishing email closely mimics the design of the official interface. However, a quick inspection of the browser address clearly shows that the website URL doesn’t match the institutional domain, universityofcalifornia.edu. Attempts to log into the site exposes your credentials to attackers who can then gain access to the real UCPath account and cause further damage.
Fortunately, the UC swiftly responded to the phishing attacks by increasing security measures in the UCPath system with no financial loss or safety repercussions as a result.
Recommended Actions
While the phishing incident is concerning, such cyber security incidents are now regular and persistent in the modern digital landscape. Be cautious of unexpected messages and stay up to date on security news as social engineering trends grow increasingly sophisticated. Proactive measures, ongoing education, and heightened vigilance remain essential in mitigating the risks posed by cyber attacks.
Do not respond or engage with a suspected phishing email. Report the suspicious activity and any potential or known breach of personal information to security@lbl.gov as soon as possible.
For other related questions, please email help@lbl.gov to open a ticket.
Check out past Cyber Security phishing articles for more tips on recognizing and preventing scams.