A new attack technique, dubbed “ClickFix,” has emerged, putting computer users at risk of compromising their own devices. This attack begins with a deceptive message or warning that appears on your screen, claiming that your computer has a problem or needs to be fixed. The message then instructs you to “fix” the issue by copying and pasting code into your computer. However, this code is malicious, and by running it, you inadvertently grant the attacker access to your computer.
How the ClickFix Attack Works
The ClickFix attack typically starts with a fake alert or popup that appears on your screen, warning of a supposed system problem that needs to be resolved. The message provides step-by-step instructions, urging you to copy and paste code into a PowerShell command prompt or the “Run” utility, claiming it will fix the issue. Here’s an example of what the popup might look like:
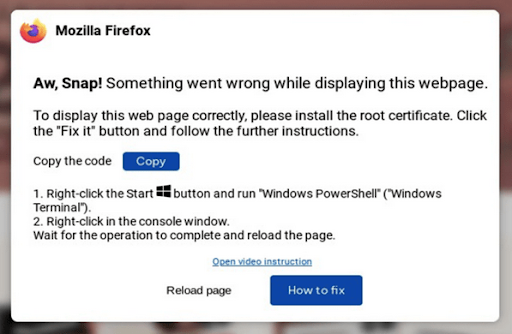
If you follow the instructions provided by the attackers, you may be directed to open either the PowerShell dialog or the Windows Run dialog. These dialog boxes are legitimate tools, but in the context of the ClickFix attack, they are red flags. If you find yourself in either of these dialog boxes, with instructions to copy and paste code, alarms should go off. This is a strong indication that you’re being targeted by the ClickFix attack and that your computer is at risk of being compromised. Do not proceed. Instead, close the dialog box and seek help.
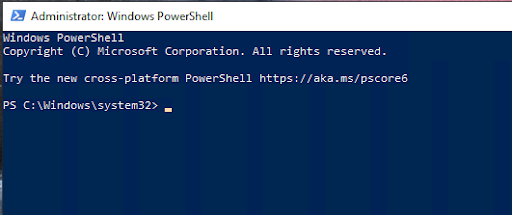
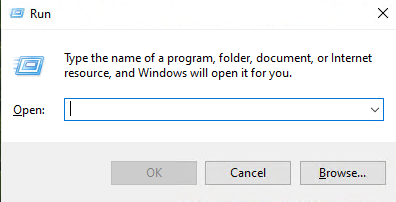
If you proceed with the attack, you’ll be prompted to paste the text you copied from the initial message into the PowerShell or Run dialog. What you’re actually pasting is obfuscated text, which is a type of encoded or encrypted code that’s difficult to read. However, when executed, this text runs malware on your computer, effectively tricking you into installing and running the malicious software yourself. At this point, the attack has successfully compromised your system, allowing the attacker to gain unauthorized access and potentially steal sensitive information or cause further harm.
Why It’s Effective
The “ClickFix” attack is notable for its clever exploitation of human psychology and everyday system tools. By presenting a fake warning message and manipulating users into executing malicious code, attackers cleverly bypass traditional security measures. The attack’s use of obfuscated code and legitimate tools like PowerShell and Run makes it difficult to detect, emphasizing the importance of user awareness and education in preventing such threats. Its subtlety and social engineering tactics make it a compelling example of modern cybersecurity challenges.
Key Takeaways
To protect yourself and the Lab against ClickFix and similar scams:
- Be aware of the “ClickFix” attack technique: This new tactic tricks users into compromising their own systems.
- Be cautious with unexpected system warnings: Be wary of unexpected warnings or messages that prompt you to take action, especially if they ask you to copy and paste code into a command prompt or terminal.
- Avoid executing unfamiliar code: Never execute code from an untrusted source, especially if you’re prompted to do so through a fake warning message.
- Be wary of prompts to open Run or PowerShell: These are not normal actions for everyday tasks, and could be a sign of a security threat.
What To Do If You’re Affected
If you think you may have followed these steps and pasted a malicious command:
- Disconnect from the internet: Immediately disconnect your device from the internet to prevent further communication with the attacker’s server.
- Do not continue using the device until it has been checked by your departmental IT staff.
- Notify your departmental IT staff or contact IT Helpdesk to report the incident. Provide as much detail as you can about what happened.
The “ClickFix” attack serves as a stark reminder of the evolving threats in the cybersecurity landscape. By exploiting human psychology and leveraging everyday system tools, attackers can bypass traditional security measures and gain unauthorized access to sensitive information.

